
PCI penetration testing is how you ensure you keep credit card data safe from attackers.
Unfortunately, the reality is that compliance doesn't guarantee security, and cybersecurity doesn't automatically mean compliance. You need both. And right now, plenty of organisations have neither.
The fines for PCI DSS non-compliance can reach $100,000 per month. But that's almost beside the point. The bigger threat is the sheer scale of the criminal industry targeting you. Ellipse reported that US ecommerce transactions were forecast to reach $1.2 trillion in 2025. Global ecommerce fraud was estimated at $50.5 billion for 2024; the fraud market is booming.
When cardholder data leaks, you’re not just paying fines, but also for:
- Forensic investigations
- Legal fees
- Customer notification
- The slow bleed of lost business as customers take their cards elsewhere
LexisNexis found that for every $1 that US financial institutions lost to fraud, it actually cost them $5.75.
This is why PCI penetration testing exists. It acts as genuine verification that your defences work against real attack techniques. The trouble is, most guidance on this topic either oversimplifies the requirements or buries them in jargon.
So, we’re getting precise about what PCI DSS Requirement 11.
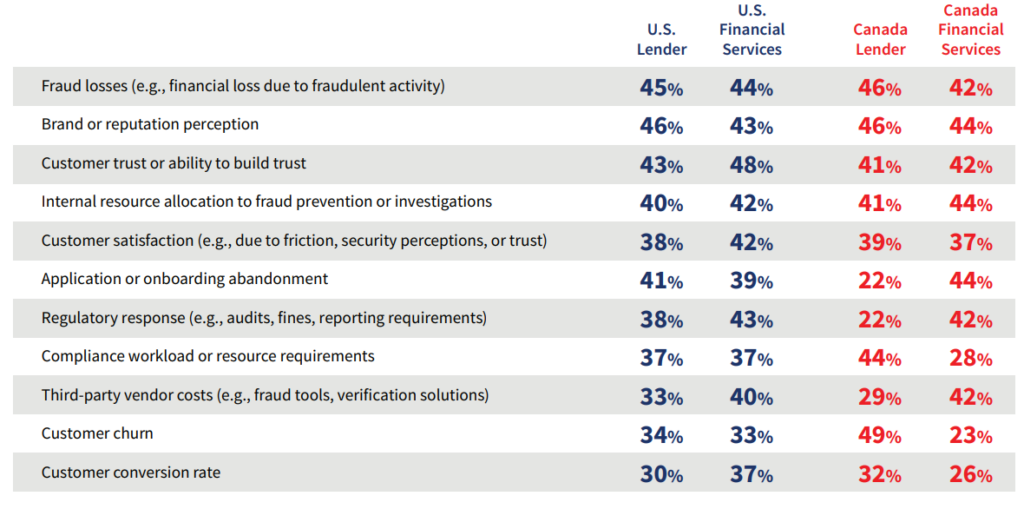
Business Areas Impacted by Fraud (by segment)
Understanding PCI DSS Requirement 11
Requirement 11 is the section of the PCI DSS framework called "regularly test security systems and processes." It’s where you prove that all the other controls you've implemented actually function as intended.
But Requirement 11 isn't a single thing. It contains several distinct obligations, and mixing them up causes real problems.
Requirement 11.2: The Automated Quarterly Scans
Requirement 11.2 mandates quarterly vulnerability scans. For external scans, you must use an Approved Scanning Vendor (ASV), a third-party certified by the PCI Security Standards Council.
These are largely automated scans. They check for known vulnerabilities, misconfigurations, and exposed services from outside your network.
Internal scans don't require an ASV, but they must still happen quarterly and after significant changes.
What These Scans Do Well
They catch known issues at scale, quickly. They'll flag unpatched systems, default credentials left in place, and services that shouldn't be exposed.
What These Scans Don’t Do
They don't think creatively. An automated scanner follows a predetermined checklist. It won't chain vulnerabilities together the way an attacker would. Scans produce false positives that need human interpretation. It misses logic flaws entirely.
The ASV scan is necessary. But it’s not sufficient.
Requirement 11.3: PCI Penetration Testing
Requirement 11.3 is different in kind, not just degree. It mandates annual penetration testing. This must also happen after any significant infrastructure or application changes. Crucially, this must be a manual, skilled exercise.
The standard explicitly requires testing that covers:
- Network-layer penetration testing (both internal and external)
- Application-layer penetration testing (for any in-scope applications)
- Testing of segmentation controls
The PCI DSS doesn't merely want you to run tools. It wants evidence that a skilled tester attempted to compromise your cardholder data environment (CDE). It wants proof that they used the same techniques an attacker would use.
This is where many organisations get confused. They see "penetration testing" in the requirement and assume their quarterly scans cover it. They don't. Or they hire a firm that runs automated tools, produces a lengthy report, and calls it a penetration test. That is not what Requirement 11.3 demands.
Genuine PCI penetration testing involves human intelligence. Testers examine your specific environment. We understand the business logic of your applications and attempt creative attack paths, and verify whether an attacker could actually reach cardholder data.
Scope Definition: What Needs Testing
Before any testing begins, you must answer a simple question: What is in scope?
The cardholder data environment (CDE) includes all systems that store, process, or transmit cardholder data. It also includes any systems that connect to them. This seems straightforward until you start mapping actual network architecture.
- Does your logging server receive data from systems in the CDE? It's in scope.
- Does your backup system touch those servers? In scope.
- Can an administrator's workstation access the CDE for support purposes? That workstation is now in scope.
Scope creep is expensive. It increases both compliance costs and testing time. This is why network segmentation matters so much.
Why Scope Definition Goes Wrong
The most common mistake we see is organisations defining scope based on where they intend cardholder data to exist. They ignore where it actually exists.
Cardholder data has a tendency to appear in unexpected places.
- Development databases populated with production data.
- Log files that capture full card numbers.
- Spreadsheets on finance team workstations.
- Backup tapes stored with inadequate controls.
Before a penetration test can be properly scoped, you need accurate data flow documentation.
- At what point does cardholder data enter your systems?
- Where does it travel?
- Where does it rest?
If you can't answer these questions, the testing scope will be wrong.
This is where a code audit can prove valuable before penetration testing begins. Understanding how your applications handle sensitive data informs where testers should focus their efforts.
Segmentation Checks: Proving Your Walls Work
Network segmentation is one of the most powerful tools for reducing PCI scope. It’s also one of the most frequently misconfigured.
The concept is simple. If you properly isolate your cardholder data environment from the rest of your network, only the isolated portion needs to meet full PCI DSS requirements. Everything else falls out of scope. This dramatically reduces your compliance burden and budget.
The catch? You must prove the segmentation actually works. And, you must do this every six months.
What Segmentation Testing Involves
Segmentation testing isn't about confirming firewall rules exist on paper. It's about verifying, through actual testing, that systems outside the CDE cannot communicate with systems inside it in unauthorised ways.
A tester places themselves on a non-CDE network segment to attempt to reach CDE systems. They try obvious paths and non-obvious ones. They look for firewall misconfigurations, routing errors, and VPN issues.
If segmentation fails during testing, you have two options.
- You can fix the segmentation.
- You can expand your compliance scope to include the connected systems.
Neither is pleasant to discover during a formal assessment.
At 7ASecurity, we conduct segmentation testing as part of both internal penetration tests and external penetration tests. We verify that your network architecture matches your compliance documentation.
The Difference Between Checking Boxes and Actual Security
Unfortunately, organisations treat PCI compliance as an annual event rather than an ongoing security posture.
They engage a testing firm, fix the findings just enough to pass, and file the report. Twelve months later, they do it again. In between, security slowly degrades. New systems get deployed without proper review. Configurations drift. Staff turnover means institutional knowledge evaporates.
Then a breach happens. Everyone is surprised that a "compliant" organisation was compromised.
PCI DSS compliance should result in better security. The controls are sensible. But the framework only works if organisations treat it as a minimum standard rather than a target.
What a Proper Testing Culture Looks Like
Organisations with strong security postures don't wait for annual PCI penetration testing to find problems. They test continuously.
- Web application penetration tests occur whenever significant functionality changes.
- Mobile application assessments happen before major releases.
- Cloud security audits verify that platform configurations remain secure.
The annual PCI test then becomes confirmation of what you already know. It shouldn't be an unpleasant surprise.
Choosing a Testing Partner
Requirement 11.3 specifies that testers must be organisationally independent. They can't test their own work, and must have relevant qualifications.
But qualifications vary enormously. Some firms run automated tools and call the output a penetration test report. They comply with the requirement’s letter while missing its spirit entirely.
Here’s what distinguishes manual penetration testing:
- Human creativity in finding attack paths.
- Business logic testing that tools can’t perform.
- Validation of findings (eliminating false positives).
- Clear remediation guidance specific to your environment.
When evaluating testing partners, ask direct questions. What percentage of your findings come from manual testing versus automated tools? How do you validate business logic vulnerabilities?
At 7ASecurity, our penetration testers conduct thorough manual assessments. We're GDPR-compliant, which is critical for any organisation handling EU cardholder data. Our detailed approach emphasises validated findings over automated noise.
After the Test: Making Findings Actionable
A penetration test report is only valuable if it leads to improvement. This seems obvious, but we've seen reports gather dust on shelves.
Quality reports provide more than a list of vulnerabilities. They explain:
- How each finding could be exploited in your specific context.
- What the realistic impact would be.
- How to remediate the issue.
- How to verify that remediation worked.
Prioritisation matters too. Not every finding is equally urgent. A critical vulnerability in your card processing application demands immediate attention, while a minor information disclosure on a marketing website can wait. A good testing partner helps you understand these distinctions.
Frequently Asked Questions About PCI DSS Pentesting
How often must PCI penetration testing be performed?
PCI DSS requires pentesting to be completed at least once a year. You must also test after any significant infrastructure or application changes. This includes new system components, firewall rule modifications, and product upgrades. If you rely on segmentation to reduce scope, segmentation testing must occur every six months.
Can internal IT staff conduct PCI penetration testing?
Technically, yes, if they are qualified and organisationally independent. This means they can’t test systems they helped build or manage.
Practically, this is difficult. Internal staff may have blind spots. Most auditors prefer to see third-party testing to ensure objectivity.
What happens if a penetration test finds critical vulnerabilities?
Finding vulnerabilities is the point. It’s better to find them during a test than during a breach. If critical findings emerge, you must remediate them. Then, you must retest to verify that the fixes work. Your report should provide specific guidance on how to fix each issue.
Let’s Discuss Your Testing Requirements
PCI DSS penetration testing isn't about satisfying auditors, but knowing that your cardholder data protections work against real attacks.
7ASecurity approaches every engagement with this perspective to make your compliance straightforward and security genuinely robust.
Ready to verify your cardholder data environment?
