Update 2022-08-22: 7ASecurity completed a comprehensive retest performed against LeaveHomeSafe 3.4.0, where most issues, including the critical one, were confirmed to remain unfixed. However, some medium severity findings were silently patched without notifying the public.
Update 2022-07-29:
In light of the public statement from the Hong Kong CIO, 7ASecurity confirmed the latest version of LeaveHomeSafe (3.3.0) remains vulnerable to all security vulnerabilities in the public pentest report. This is despite more than 30 days having passed since the report was first shared with the Developer and OGCIO on 2022-06-24. Who have not issued an update for the application since 2022-06-02 (i.e. before the report was shared). Live demos of some of these issues carried out since the report’s release, along with additional background information, can be seen in the 7ASecurity YouTube Channel.
Political Background
The background of this project is to address the general concern about the potential security and privacy risks that might be introduced by the LeaveHomeSafe Android and iOS applications. This app was introduced by the Hong Kong Government in November 2020 and saw limited adoption to start. Less than half a million downloads occurred in the first two weeks. This was in part due to privacy concerns of Hong Kong Citizens. Many of whom acquired second mobile devices in order to avoid having sensitive content on the same phone.
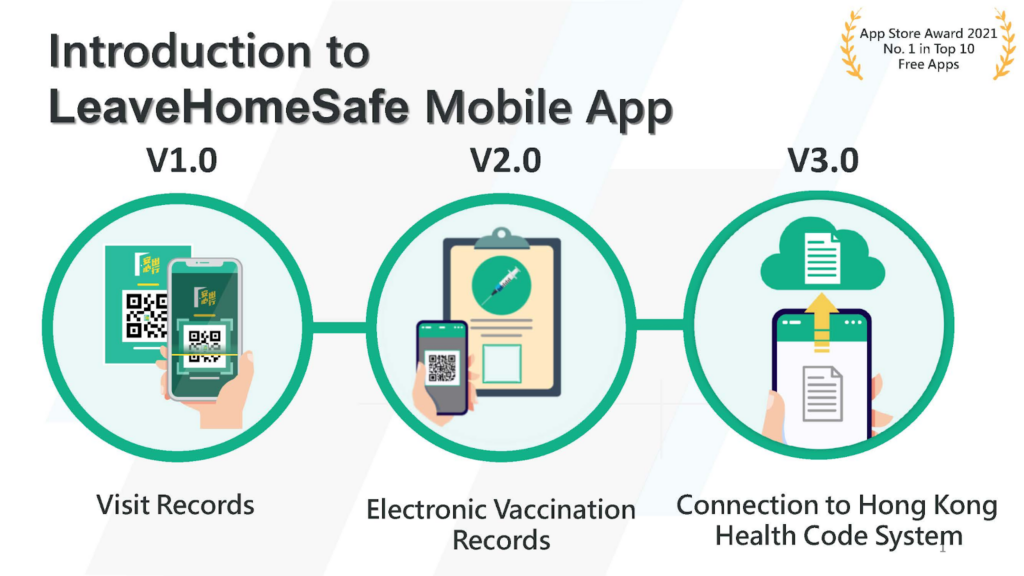
Fig.: Functionality introduced in each LeaveHomeSafe release
As a result of these concerns, an updated version of the app reportedly reduced the permissions the app was requesting from 15 to 7. An accompanying statement related to privacy was issued stating in part that the app complies with the Personal Data Ordinance. External analysis conveyed the same message. By February of 2021, the government allowed restaurants to expand operating hours until 10 pm and four patrons at one table provided that diners download “LeaveHomeSafe” App or register personal information by hand. Sports facilities, fitness centers, beauty salons, and public entertainment places were also allowed to resume operation if they displayed the LeaveHomeSafe App and helped register the personal information of customers.
This policy evolved to require use of the app. This change was encouraged by the Chinese government which wanted a curb in second phone use and a policy for real-name registration. Starting in November 2021, the government forced citizens entering government buildings or offices to scan the QR code prior to entering. The following month a mandate was issued that the app must be used to enter all government venues, hospitals, markets, hotels, cinemas, restaurants, gyms, shopping malls, supermarkets, universities and places of worship, among others. Restaurant employees are also required to be vaccinated under the policy.
Enforcement agents can “request customers to show the login page of the LeaveHomeSafe App” when inspecting the premises of covered entities. If someone does not have the app installed they face a fine of 5,000 HKD ($637) for each violation. Furthermore, if investigators find that patrons do not have the app installed the restaurant will be downgraded to a Category A business model. This means they can only operate between 5am and 6pm, with no more than two persons at one table, whereas Category D restaurants can operate till 2am and have up to 12 people per table.
These actions have unsurprisingly resulted in a substantial segment of the population installing the app. In late June, the IT Minister stated it had received more than 8 million downloads. It is also frequently found in the most popular apps in the Hong Kong market. Despite these efforts, questions have been raised around the overall amount of downloads being artificially inflated. Given that the entire Hong Kong population is 7.5 million, it is clear that the app is also being downloaded elsewhere.
In order to encourage adoption, the government has sought to alleviate privacy related concerns through public statements. In November 2020, a release entitled “New app's data privacy assured” stressed “that the data will be encrypted” and “adopts the AES-256 encryption standard to protect the travel records saved in users' mobile phones.” In February 2021, another press release was issued which stated that “The app does not pose a risk to privacy” and “members of the public can feel at ease when using the app.” They went on to state that “the app has undergone and passed security risk assessment and auditing as well as privacy impact assessment conducted by independent third parties to ensure its compliance with the Personal Data (Privacy) Ordinance.” A message that was repeated in June after the inclusion of functionality to display vaccination records which required the collection of “relevant personal information.”
The security and privacy assessments of the app were performed in October of 2021. The privacy audit states “Overall, no issue or potential risk that may cause privacy data breach is identified after a detailed privacy impact analysis has been conducted.” The security audit similarly states “In general, security controls are found properly in place to protect LHS, their data and related infrastructure and the System are in compliance with the prevailing IT security regulations, security policies, standards, guidelines and procedures of the Government and OGCIO [Office of the Government Chief Information Officer].”
A May 2022 statement promised to “proactively explain the information security and privacy protection aspects of the "LeaveHomeSafe" mobile app to the public.” The statement was in response to an investigation of the app by journalists at FactWire, an independent news outlet based in Hong Kong. The outlet reviewed the Android app’s source code and found evidence it has facial recognition capabilities. Subsequently, the OGCIO claimed that it had asked the app’s developer, Cherrypicks Limited, a subsidiary of the Chinese online gaming company NetDragon Websoft, to look into removing the facial recognition source code without affecting the “normal operation” of the application.
More recently there have been reports that the government has begun requiring people to register by name in the app along with tracking and restricting movement of infected residents and close contacts through a traffic light color code. This is a marked shift from having the option to provide personal information in person and not provide personal details inside the app. The real name registration requirement has been a long standing aim of the Chinese government. The implementation of the color code system also fueled additional concerns around privacy and social control given that mainland Chinese authorities used a similar system to prevent residents from attending a planned protest.
The Audit
The goal of this engagement was to have an independent third party verify whether the official LeaveHomeSafe privacy and security claims, prominently presented on the app homepage, are accurate. 7ASecurity downloaded and reviewed the official LeaveHomeSafe Android (3.1.0, 3.2.0, 3.2.3) and iOS (3.1.0, 3.2.0, 3.2.3) applications, which were the latest available during this assignment.
The methodology implemented was blackbox. The 7ASecurity team had no access to test users, documentation or source code. The lack of Hong Kong Health Code System credentials, valid vaccination status QR codes and valid COVID testing status QR codes were major limitations during this assignment, as the testers could not fully exercise the application logic in those functional areas. All efforts were therefore focused on reverse engineering, decompiling the applications and analyzing their behavior at runtime. A team of 4 senior testers was assigned for the preparation, execution and finalization of this project.
All preparations were done in March and April of 2022, ahead of the test, to ensure a smooth start for the 7ASecurity team. Communications during the test were done using a shared Signal chat group. The Hong Kong Democracy Council (HKDC) and OTF were helpful and responsive throughout the audit.
Regarding the security audit (WP1), the team acquired adequate coverage over the scope items and managed to spot a total of 12 findings, 8 of which were classified as security vulnerabilities and 4 as general weaknesses with lower exploitation potential. Please note that 3 of the findings in this report had an estimated severity level of high or critical. This poor result strongly suggests that the LeaveHomeSafe mobile apps have not been audited by any competent security firm previously. This is in stark contrast to the documentation in the official LeaveHomeSafe website, which indicates the mobile applications were audited previously on December 10th 2021, and only a single “low” priority issue was identified.
Regarding the privacy audit (WP2), a concerning privacy-related finding was the presence of face recognition libraries. While the FactWire article found only usage of React Native Face Detector, 7ASecurity found both Google Face detector, as well as React Native Face Detector. Even though usage of these libraries could not be proven at runtime, the obvious question of why are these libraries present in the codebase? must be asked.
Conclusion
This exercise involved both a privacy audit and a security audit of the LeaveHomeSafe Android and iOS apps. The privacy audit could not conclusively prove malicious intent or unauthorized tracking of Hong Kong citizens. However, the security audit demonstrated that these applications have not been professionally audited by any competent security firm before, and that significant flaws exist in the current software security development lifecycle. This is particularly concerning given that the app was originally introduced more than a year and a half ago, was made mandatory in some fashion for 9 months and recently began requesting real name registration and tracking user’s movements.
While no clear privacy violation could be conclusively proven during the audit at runtime, a number of application artifacts, likely inherited from underlying dependencies or simply security vulnerabilities introduced by mistake, were found during this exercise.
7ASecurity would like to thank the Hong Kong Democracy Council (HKDC) for their project coordination, support and assistance, both before and during this assignment. Last but not least, appreciation must be extended to the Open Technology Fund (OTF) for sponsoring this project.
In the interest of full transparency, the pentest report is now public and available for download.
Disclosure Timeline:
2022-06-24 - Initial disclosure email attaching the full pentest report
2022-06-24 - Automated acknowledgement received
2022-07-04 - Friendly disclosure reminder follow-up sent, attaching the pentest report again
2022-07-04 - Automated acknowledgement received
2022-07-12 - Friendly disclosure reminder follow-up sent, attaching the pentest report again
2022-07-12 - Automated acknowledgement received
2022-07-19 - Friendly disclosure reminder follow-up sent, attaching the pentest report again
2022-07-19 - Automated acknowledgement received
2022-07-26 - Public Disclosure
2022-07-28 – An official Government response is issued: [...]The OGCIO expressed deep regrets and strongly opposed to the inaccurate report and unfair accusation.
2022-07-29 – 7ASecurity confirms LeaveHomeSafe 3.3.0 was released on 2022-06-02, 22 days before the report was shared, strongly suggesting nothing was fixed.
2022-07-29 – 7ASecurity further validates LeaveHomeSafe 3.3.0 (the latest version) remains vulnerable to (at least) the highest impact findings, and demonstrates some of those using live demos on the 7ASecurity YouTube Channel.
