
The Smart Way to Secure Your Online Presence
Think web application penetration testing is an unnecessary business expense? Let's look at the numbers.
According to IBM's 2025 Cost of a Data Breach report, the global average cost of a data breach has reached an eye-watering $4.44 million. While it’s lower than in 2024 ($4.88M), thanks to improved and proactive cybersecurity measures, it’s hardly small change.
For many businesses, their web application is their digital front door. It’s how customers interact with them, how data is managed, and how sales are made. Unfortunately, it's often also the most exposed and vulnerable asset.
You probably have firewalls and other defences in place. But how do you know they actually work against a determined attacker?
This is where web application penetration testing gives you certainty. Think of it as a controlled, ethical hack designed to find weak spots before the real criminals do. It’s a critical health check for your online presence.
What is Web Application Penetration Testing?
Let's break it down. Imagine you own a bank and want to be sure your new vault is secure. You wouldn't just trust the brochure, right? You'd hire an expert to try and break into it.
That's exactly what web application penetration testing does. We get your permission to simulate a real-world attack on your application to find exploitable security flaws.
This isn't about running a simple automated vulnerability scan that spits out a long list of potential problems. These scans regularly miss important holes and give many false alarms.
Our cybersecurity experts test your systems "like the bad guys" would. We use our creativity and expertise to uncover issues that automated tools almost always miss.
The Process: How a Web App Pentest Works
A thorough security audit follows a clear, structured path.
Scoping and Reconnaissance
First, we define the scope of the test with you. Then, our pentesters gather information about your application.
They map out its structure, identify its technologies, and understand how it functions. This reconnaissance phase helps them think like an attacker and spot potential areas of weakness.
Controlled Attacks
Next, the testing begins. Our experts attempt to bypass security controls and exploit vulnerabilities in a safe, controlled manner.
We test for critical security risks, like those identified in the industry-standard OWASP Top 10. These include things like injection flaws and broken access controls. (Our CEO, Abraham Aranguren, is an OWASP OWTF project leader, so we’re always up-to-date on industry standards and changes.)
A controlled attack is a hands-on approach that reveals what could actually happen in a real attack, but without the fallout of a real data breach.
Analysis and Reporting
Finally, we document everything. You receive a to-the-point report that clearly explains the vulnerabilities we found, the risks they pose to your business, and the technical details your developers need to fix them.
No fluff, just actionable insights.
Annual number of cyberattacks worldwide from 2016 to 2024
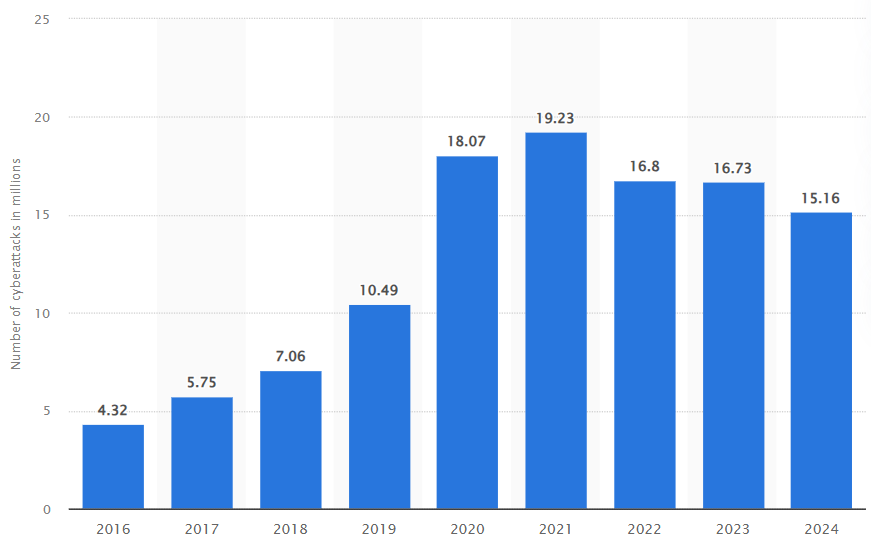
Caption: The number of global cyberattacks remains high, with over 15 million incidents recorded in 2024 alone. Another reason for proactive cybersecurity measures.
Source: Statista
Why is Penetration Testing on a Web Application So Important?
Still wondering why this matters for your business? It comes down to three simple things:
- Protection
- Reputation
- Regulation
Find Vulnerabilities Before Attackers Do
The most obvious benefit is finding and fixing security holes before they're exploited.
Cybercriminals are constantly looking for easy targets with common flaws like SQL injection, broken authentication, or security misconfigurations.
A penetration test identifies these weak points so you can strengthen your defences. It's a proactive step that puts you back in control of your security.
Protect Your Reputation and Your Bottom Line
A data breach can be devastating. Beyond the immediate financial costs of fines and recovery, the damage to your brand can be permanent.
Customers trust you with their data. A security incident shatters that trust and can send them straight to your competitors.
A proper security audit is an investment in business continuity and brand reputation.
Meet Regulatory and Compliance Requirements
Strict data protection regulations govern most industries. Regular security testing is often a primary requirement for compliance.
Staying Compliant with GDPR, SOC 2, and PCI DSS
Frameworks like GDPR for data privacy, SOC 2 for service organisations, and PCI DSS for payment card data all require organisations to implement and validate strong security controls.
Penetration testing on a web application serves as powerful proof that you are taking your security obligations seriously.
The Benefits of Regular Web App Penetration Testing
Security isn't a one-time project. It’s an ongoing process.
A Continuous Security Posture
Your application is constantly evolving. New features are added, and your code is updated, which means fresh threats appear every day.
That's why we recommend annual testing, or even more frequently if your application undergoes significant changes.
Regular testing helps you maintain a strong and continuous security posture, adapting your defences as your business grows.
Beyond the Report: Verification and Peace of Mind
Finding a vulnerability is only half the battle. You also need to be sure it has been fixed correctly.
At 7ASecurity, we provide a free fix verification after our tests. This ensures the gaps have been truly closed, giving you confidence that your application is secure and your business protected.
Secure Your Digital Front Door. For Good!
Your web application is a vital part of your business. Is leaving its security to chance really a gamble you can take?
Our professional web application penetration tests aren’t mere scans. We conduct a deep, expert-driven analysis to give you an accurate picture of your security. So, your team can stop threats before they happen.
Ready to find out how secure your application actually is?
