UPDATE: 10/10/2014 - Added link to OWTF 1.0 "Lionheart": Automated Rankings
OWTF 1.0 "Lionheart" (beta) is dedicated to everybody that helped make this challenging release happen, in particular to the courage of all this people, who overcame their sweat, blood and tears to make OWTF the amazing tool it is now, to all of you, thank you!
OWTF 1.0 "Lionheart" (beta) is dedicated to everybody that helped make this challenging release happen, in particular to the courage of all this people, who overcame their sweat, blood and tears to make OWTF the amazing tool it is now, to all of you, thank you!
We would like to take this opportunity to thank all contributors, mentors, everybody who sent us cool ideas, feedback or reported bugs, you all played a role in making OWTF be what is is now, many thanks to you all!.
Some links:
- Getting started
- Downloading & Installation
- Documentation
- OWTF 1.0 "Lionheart" playlist on Youtube
- Try some of the OWTF features from your browser 🙂
- Please give us feedback / suggestions / report bugs
- Join us on IRC (#owtf on Freenode)
OWTF 1.0 “Lionheart” (beta) is our biggest release ever, this contains many cool projects implemented by many , so, in no particular order, here is a quick overview of the new major features! 🙂
NOTE: For a more detailed explanation please see OWTF 1.0 "Lionheart": Automated Rankings
When testing a bunch of web applications, OWTF will append the ranking associated with each target for an easy quick overview.
More information can be retrieved when accessing to one specific target report. Here, OWTF uses labels and color codes to help the user reviewing the results.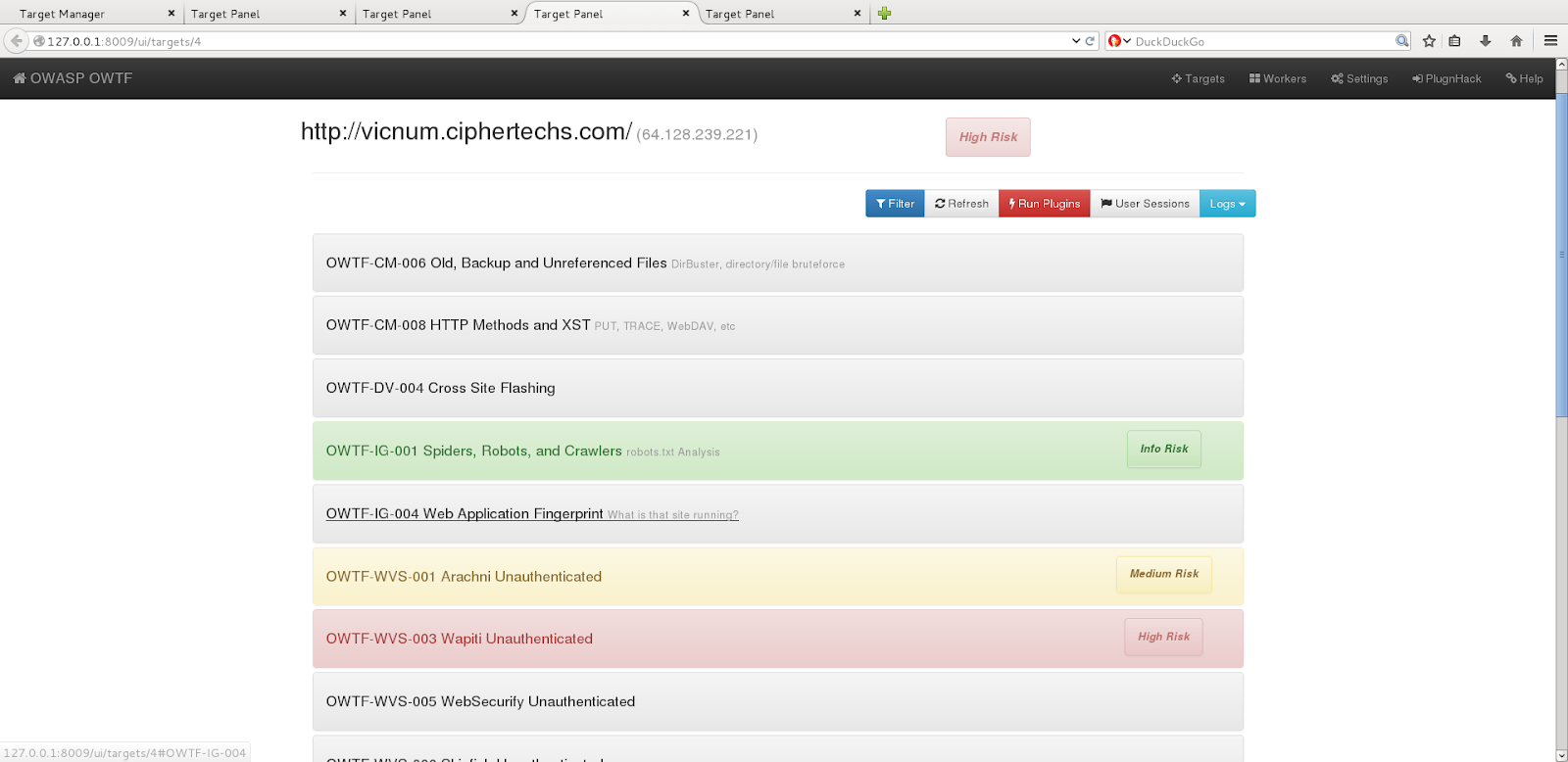
Sexy Web UI + REST API + Database by Bharadwaj Machiraju
-
OWTF now features a Web UI from where you can run scans, plugins, etc.
-
RESTful API to send commands to OWTF!
-
Highly performant postgres database
Zest support and ZAP integration by Deep Shah
-
Interactively send HTTP requests to a target
-
Record and play Zest scripts
-
Pass interesting HTTP requests to ZAP using the ZAP API
WAF bypasser by Marios Kourtesis
Detecting blocked characters and searching for bypasses:
Fuzzing with XSS payloads:
OWASP OWTF - State Improvements by Viyat Bhalodia
-
HTTP Sessions (Cookie based) detection
-
Ability to change sessions using Zest Integration
Improved Plug-n-hack support by Punga Cornel
Plug-n-Hack is a proposed Mozilla standard.
Now OWTF supports Plug-n-Hackv2, which allows you to intercept, change and fuzz client side messages!
Now OWTF supports Plug-n-Hackv2, which allows you to intercept, change and fuzz client side messages!
Online passive scanner, Boilerplate templates and Flexible Mappings by Anirudh Anand
- Online Boilerplate templates: Easy to copy-paste stuff into your pentest reports (i.e. mitigation, etc.)
- Passive Online scanner: Try some of the OWTF passive tests without installing anything! 🙂
- Flexible mappings: OWTF will now let you view plugins by OWASP Top 10, OWASP Testing Guide v4, OWASP Testing Guide v3 and even NIST! 🙂
